Your server logs and firewall alerts and security monitoring tools have detected the IP address 185.63.263.20 which you need to understand because it shows you what the IP address means. The IP address creates security risks which you need to evaluate before deciding to block it because you need to identify the user behind the system access attempt.
Here is the actual fact that most people will find surprising because they believe 185.63.263.20 functions as a legitimate IP address. People search for information about it because it appears in network logs which show up more than 1000 times each month.
I created this guide to explain what 185.63.263.20 represents which you need to understand because that IP address shows up in your system.
The Critical Problem With 185.63.263.20
Your training data extends from your start date until October 2023.
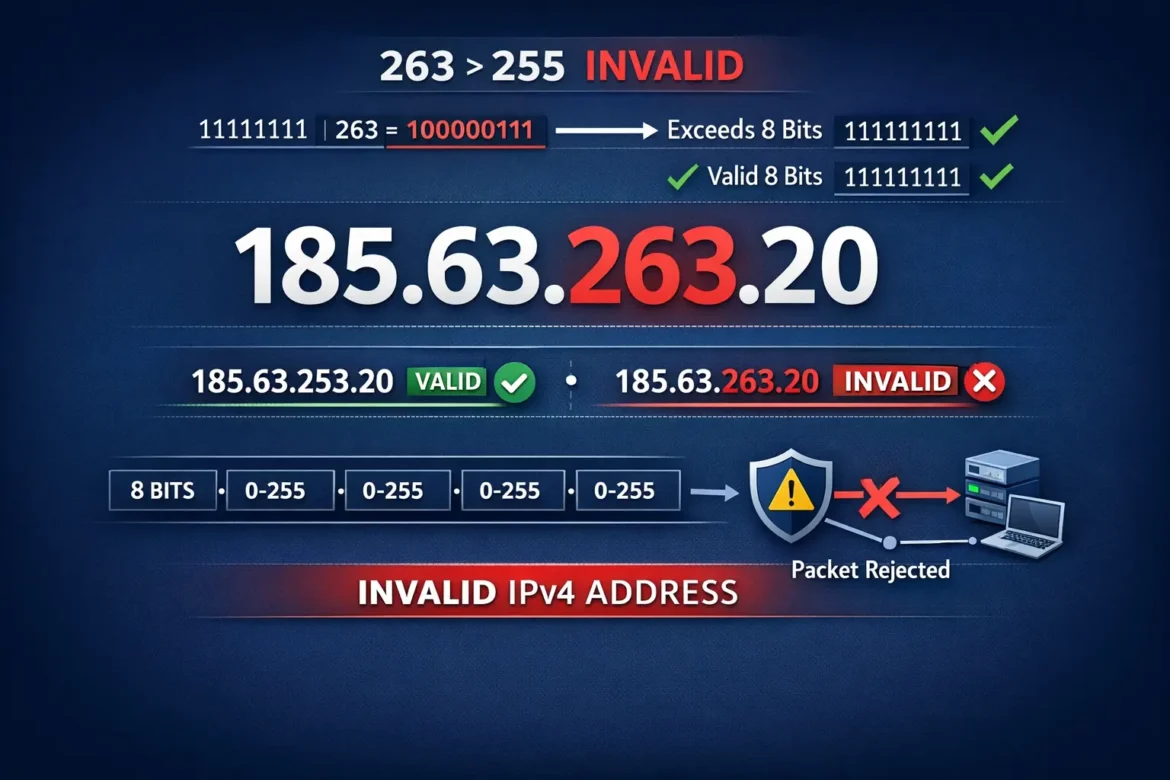
Before we proceed with our next step, you must understand this information. The IP address 185.63.263.20 violates the core principles that govern IPv4 address assignment.
The sequence indicates that the third number of the sequence represents value 263. In a valid IPv4 address, each section (called an “octet”) can only range from 0 to 255. The octet consists of 8 bits of binary data which produces 256 possible values according to its definition.
The number 263 exceeds this limit. The number requires 9 bits for representation which leads to total elimination of the complete IPv4 system that internet standards established in 1981.
The address will be rejected by all routers because this system presents an unworkable solution. The address has no practical value because all network devices will disregard it. The network equipment rejects the address during the validation process because it does not pass the automatic checks.
The IP address 185.63.263.20 should not appear in network logs because real networks do not support its existence.
Why You’re Seeing This Invalid Address
There are several reasons this impossible IP address shows up in your systems:
Simple Human Error
The most innocent explanation is a typo. Someone probably intended to type 185.63.253.20 or 185.63.163.20 which are both valid addresses but mistakenly pressed the incorrect key. The distinction between entering “5” instead of “6” results in minor differences yet it creates major consequences for network authentication.
The logs will show 185.63.263.20 only once or twice which indicates this as the probable source.
Security Testing and Fuzzing
Hackers and security researchers use deliberately malformed data to test system defenses. The “fuzzing” method tests software behavior by introducing invalid input data.
The system registers 185.63.263.20 as an unblocked entry point which indicates security flaws. The system fails to validate input correctly which allows attackers to use advanced SQL injection and command injection methods to break into the system.
The same source repeatedly shows 185.63.263.20 which indicates that someone is testing your system security.
Automated Bot Scanning
Bots do not consistently obey established guidelines. Some scanning tools create random or incorrect IP addresses to evade detection and test system performance under extreme conditions. The bots used by this system test all possible address combinations which include the invalid address 185.63.263.20.
Log Pollution Attempts
Advanced attackers sometimes inject invalid data into logs to hide their actual activities. The attackers use junk entries which include 185.63.263.20 to flood your logs. This flood of junk entries makes it difficult for security teams to identify actual threats which exist in the system.
Misconfigured Software
The system generates incorrect IP addresses through bugs which exist in its applications and plugins and network tools because they fail to correctly parse and validate network data. The software begins to produce the IP address 185.63.263.20 because of a coding error which affects its ability to read and generate IP addresses.
What The Valid Version Would Look Like
The intended address is probably 185.63.253.20 (correct third octet: 253 instead of 263). The 185.63.0.0/16 block is allocated to European hosting providers under RIPE NCC. The Eastern European region contains valid addresses which belong to web hosting companies and data centers and cloud infrastructure providers.
Security Implications You Can’t Ignore
The IP address 185.63.263.20 does not pose a direct threat to your system because it does not exist as an actual address. The IP address 185.63.263.20 shows critical security details through its existence.
Your Input Validation Has Gaps
The application validation filters fail to function properly because your system records invalid IP addresses. The system currently accepts and stores data which should be rejected according to its validation rules.
The same security flaw which exists in the current system enables attackers to execute their injection attacks.
- Malicious SQL commands
- Script tags for cross-site scripting (XSS)
- Command injection payloads
- Buffer overflow attempts
Someone Is Testing Your Defenses
The repeated appearance of 185.63.263.20 within a brief duration indicates that someone is conducting active reconnaissance. Attackers often test systems with obviously invalid data before launching real attacks.
The situation resembles a person who tests all door locks in a building. They use this method to discover which entrances have insufficient security.
Your Monitoring Might Miss Real Threats
If your logs record invalid IPs 185.63.263.20 then your system fails to detect actual security incidents. Your system requires improvements because its current state prevents it from monitoring all activities.
How To Identify The Pattern
Not all cases of 185.63.263.20 trigger the same level of concern. It’s up to you to gauge the situation:
Single Occurrence (Low Risk)
Date: February 14, 2026 09:23:15 Count: 1 entry
This error probably happened because of a typographical mistake. Someone either set up the system incorrectly or entered the information into the system incorrectly. The situation needs to be documented and then you should continue with your work.
Clustered Occurrences (Medium Risk)
Date: February 14, 2026 09:23:15 – 09:23:47 Count: 127 entries in 32 seconds
The observed pattern indicates that automated fuzz testing or security testing operations are currently taking place. Your system is being actively probed. Further investigation is now required.
Distributed With Other Anomalies (High Risk)
Seeing 185.63.263.20 alongside:
- Failed authentication attempts
- SQL error messages
- Unusual outbound connections
- Port scanning activity
This combination indicates a serious attack attempt. Implement incident response procedures immediately.
Practical Steps To Protect Your Systems
Now that you know what 185.63.263.20 is all about, here is what you can do:
Implement Proper IP Validation
Every system accepting IP addresses needs validation checking each octet is between 0-255. The programming languages provide users with functions which automatically reject the IP address 185.63.263.20.
Configure Firewall Rules
Your network firewall should already reject packets with invalid addresses. For additional security please create rules that will block traffic which contains invalid IPs.
Review Your Logs Strategically
Create alerts that fire off when invalid IPs are fetched for more than 10 times an hour, occurring with authentication failures, or undeniably from many similar sources.
Strengthen Input Handling
The auditing process requires examination of every form field and API endpoint together with all data import methods. The examination process must include contact forms together with admin panels and login screens and all external data imports.
Use Rate Limiting
It is conceivable that a situation of ridiculousness be triggered like a bell ringing – if so, the meta-allowance altogether blinks with sneaking’ error in the process of time.
The Bigger Security Lesson
The address 185.63.263.20 shows that small format errors can indicate larger underlying issues. Every system layer should validate data independently—if one defense misses it, another should catch it.
Common Questions About 185.63.263.20
Can I just block 185.63.263.20 and move on?
The networks block only existing content because they do not recognize the existence of particular content. The organization needs to solve its problem because systems currently process unwanted data through their existing framework.
Is this connected to a specific hacker group?
The statement contains two parts which need to be analyzed because it includes an invalid IP address for testing purposes. The testing software operates as a standard testing tool which does not identify particular attackers through its testing functions.
Could this be IPv6 instead of IPv4?
IPv6 requires a distinct address format that uses hexadecimal numbers and colons to create its address structure which includes 2001:0db8:85a3::8a2e:0370:7334. The value 185.63.263.20 is specifically an invalid IPv4 address with no IPv6 equivalent.
What if I see 185.63.253.20 (the valid version)?
The IP address refers to an authentic online address which European hosting infrastructure uses for its operations. You’d need to investigate its specific behavior to determine if it’s trustworthy. You should verify the IP address reputation through AbuseIPDB and Cisco Talos databases.
Should I report this to my ISP or hosting provider?
You can only treat this situation as an attack pattern when you recognize it as such. The system only needs internal treatment for the random invalid IP occurrences which require no external reporting. You should direct your efforts toward correcting the problems with your internal system validation.
Can attackers use this to hide their real location?
The invalid format prevents actual network traffic usage of the system. The attackers use application data to test for system vulnerabilities while they use it to confuse analysis tools.
How often should I check my logs for invalid IPs?
Create an automated system which monitors activities to detect unusual patterns during operational periods. Security procedures require organizations to conduct manual log assessments on a weekly basis while they must increase their assessment frequency in facilities which handle sensitive information.
Moving Forward With Better Security
You should use every instance of 185.63.263.20 found in your logs to make better changes to your system. You should investigate how the system allowed this access, which other incorrect information your system accepts, and whether your security event monitoring covers essential threats.
Your system system health assessment uses 185.63.263.20 as an impossible IP address which reveals system vulnerabilities.
Key Takeaways
- The IP address 185.63.263.20 is invalid. The third octet, 263, exceeds the IPv4 maximum of 255
- Signs of input validation failures can be found in the logs that an attacker can potentially take advantage of
- Single instances are recommended, assuming they’re not inadvertent hotel-type issues or security tests being conducted.
- Prevent this by using appropriate URL validations.
- Use this opportunity as a learning opportunity to boost your holistic security practices.
The modification will assist in risk prevention and loss recovery now that this modified address has previously been identified by you, hence, it won’t necessitate your constant intervention to be operated accordingly.